COMPUTER ETHICS AND SECURITY RISKS
COMPUTER ETHICS

What is Netiquette?
- Netiquette,(short for Internet etiquette), is the code of acceptable behaviors users should follow while on the Internet.
- Netiquette is the code of acceptable behavior.
| www |

- WWW
- Newsgroup
- Online Discussions
- FTP
- Chat room/Online chat
- Instant messaging
- Social Media
COMPUTER SECURITY
Any action that could cause a loss or damage to computer hardware,software,data,information and processing capabilities.
- Malware is a malicious software,which are programs that act without a users knowledge purposely alter the computer's operations.
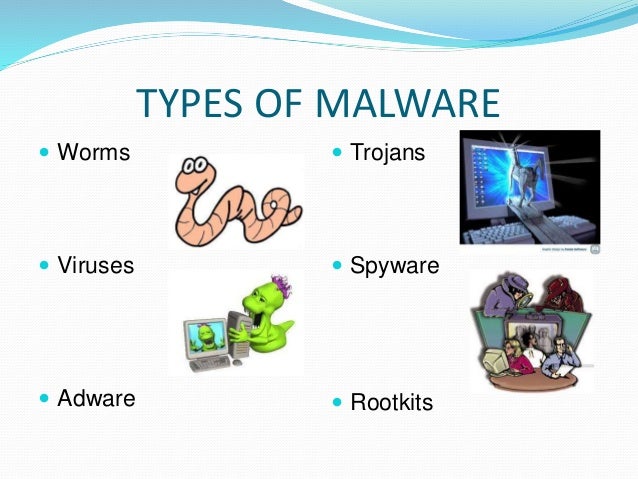
COMPUTER VIRUSES
A potentially damaging program that affects or infects a computer or mobile devices negatively by altering the way the computer or devices works without user's knowledge or permission.
- Spread throughout and may damage files and system software,including the operating systems.
A program that itself repeatedly,for example in memory,using up a resources and possibly shutting down the computer,devices or network
Trojan Horse
A program that hides within or looks like a legitimate program.Unlike a virus or worm , a trojan horse does not replicate itself to other computer or device.
It usually appears to be a game or utility programs.
Cannot replicate itself.Must be downloaded or installed.
Can sabotage a computer without users knowledge , such as installing rootkit or turning the computer into a botnet.
UNAUTHORIZED ACCESS AND USE

UNAUTHORIZED ACCESS
- Is the use of computer network without permission
- Is the use of computer , or its data unapproved or possibly illegal activities.
HARDWARE THEFT AND VANDALISM
HARDWARE THEFT
- Is the act of stealing computer equipment.
- Is the act of defacing and destroying computer equipment.
| Hardware is stolen from an individual or from a business,school or other organization. |
SOFTWARE THEFT
- STEALS SOFTWARE MEDIA
- INTENTIONALLY ERASES PROGRAM
- ILLEGALLY COPIES A PROGRAM
- ILLEGALLY REGISTERS AND/OR ACTIVATES A PROGRAM
| An dishonest library assistant might steal Encyclopedia Britannica optical disc. |
| A programmer is terminated from , or stop working for a company , and intentionally remove or disable the program they have written from company computers. |
ILLEGALLY COPIES A PROGRAM
| A software is stolen from software manufactures |
ILLEGALLY REGISTERS AND/OR ACTIVATES THE PROGRAM
- Users illegally obtaining registration numbers and/or activation codes using a program called a KEYGEN ,shot for KEY GENERATOR.
INFORMATION THEFT
Occurs when someone steals personal or confidential information.
IDENTITY THEFT
- to purchase goods or services
- to obtain new credit cards or bank loans.
- illegally pretend to be as individual
PHARMING
- Creating a fraudulent website which is identical to the original website and asking the user to key in their personal details into the website.
PHISHING
- A link created in an e-mail to request that customers update their personal details,at the same time revealing their password and credit card number.
SYSTEM FAILURE
System failure is the prolonged malfunction of a computer system.
Cause a loss of hardware , software , data and information.
Comments
Post a Comment